Featured
Table of Contents
The Ultimate Beginners Guide To Vpns
Another factor to consider in picking a VPN is how strong the file encryption is. 256-bit file encryption is basic in the VPN industry, although some companies provide less-secure 128-bit file encryption.
To see how many are on deal, look for a section on the provider's site entitled "Server List" or comparable - what are some factors to consider when choosing a vpn provider. This need to reveal you a total list of all the servers that are offered and their places. Generally speaking, more servers is better as it gives you more options to find a quick and dependable server when you connect.
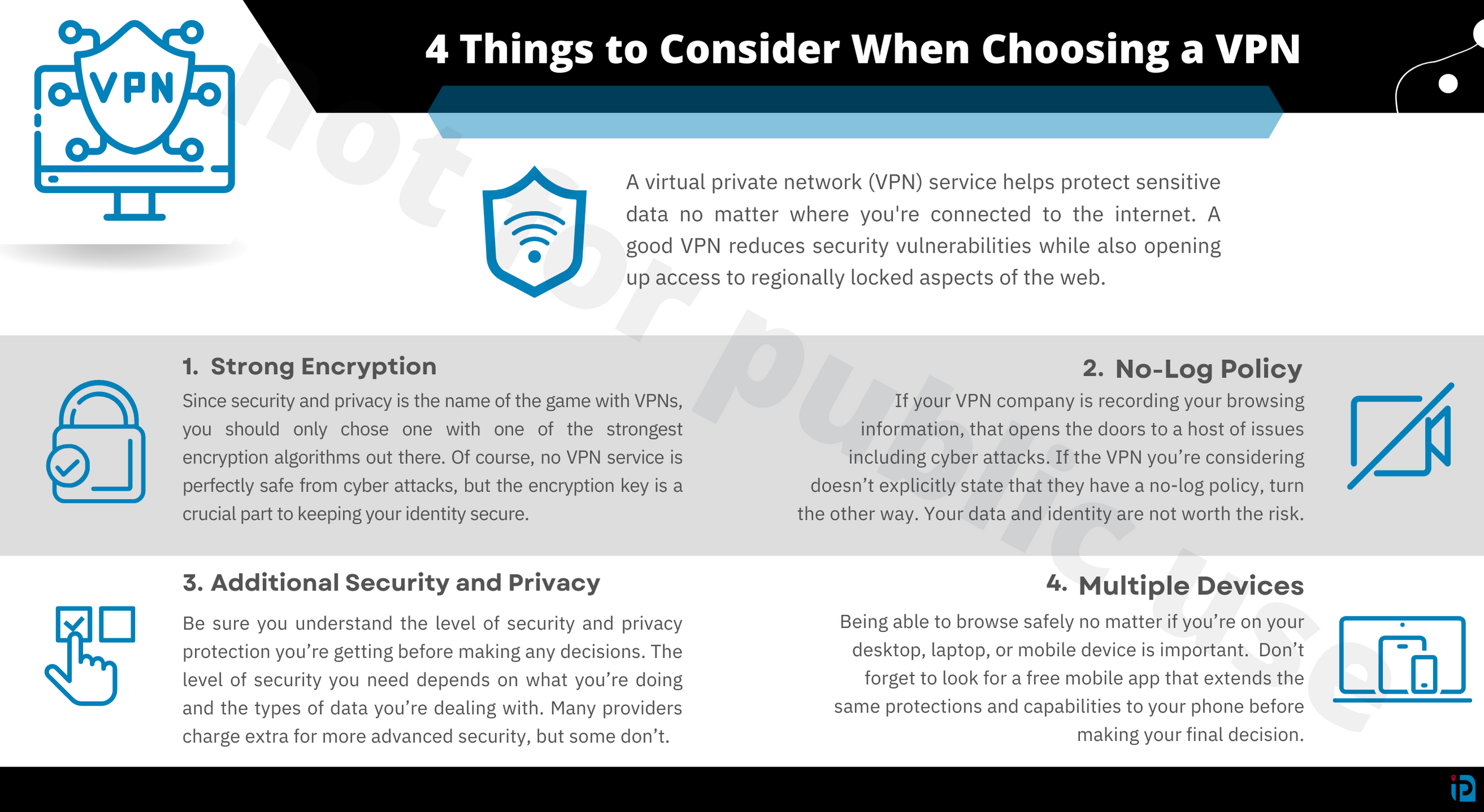
Just try to find a company with a minimum of 500 servers which must be more than enough for the majority of people. You will also desire to check how many nations servers are offered in. You can use a VPN to get around regional limitations as long as your company has a server in the nation you desire to access the web from.
What Is A Vpn? - Virtual Private Network Explained
One downside to using a VPN is that it can decrease your internet connection a little due to the additional file encryption step that the information goes through. To lessen this downturn, you'll desire a VPN that has fast servers. It can be tough to discover out how quick a VPN will be.
You can search for VPN reviews which normally include a speed test, however bear in mind that your experience will be different from somebody else's. This is due to the fact that the speed of your connection will depend upon both where you lie and where the server that you are linking to is situated.


Lots of VPN service providers provide a free trial or a money-back warranty to try their servers for a couple of days and see if you more than happy with the speeds before devoting to one company. Before you decide, you can also examine what optional features a VPN service provider offers by inspecting their site.
The Best Vpn Services For 2023
They are the core innovation that determines how your data is routed to the VPN server. There are a variety of significant VPN procedures, and they are not produced equivalent. You ought to check which VPN protocol a provider supports. Don't stress if you aren't skilled with VPN protocols. We have an extensive contrast of the major VPN procedures to make it simple for you to put everything in perspective.

Take the time to discover the ideal VPN for youstart with our guide to the best VPN services. Follow our links and conserve on a subscription!.
At minimum, we can assume all users have the exact same IP address (due to being connected to the exact same server) and therefore have the very same "exit node." This makes it harder for the various websites, web services, or web apps to select who is who, even if several users go to the same website at different times (best practices when choosing a vpn provider).
Advantages And Disadvantages Of A Vpn
In many cases, complimentary VPN providers have actually shared data with cloud service providers, governments, and anybody ready to provide some money in exchange for the data; they have actually also been accused of utilizing device resources, such as CPU power, to mine crypto for themselves (cryptojacking)! Among the most crucial things to search for in a VPN service provider is the contents of their data personal privacy - particularly data collection and any possible retention of collected information - policies.
If the VPN service provider gathered PII, then these logs could be utilized and connected back to a user's true identity. Efforts of openness can prove essential to note. It's frequently worth digging deeper than what the marketing claims (or easily neglects) on the VPN supplier's site, thinking about questions such as: Does the VPN company provide an openly available audit of their no-logs claims? Exist transparency reports that disclose demands received by government entities? What was the date of the last audit? Is an audit on a VPN supplier's no-logs policy performed routinely? Does the VPN supplier share information - such as logs - with third parties (which can include server infrastructure service providers and government entities.) Details required at signup Demands for personal recognizable info (PII) may be spun to appear innocuous - a courtesy of the VPN's marketing department.
To reduce this, relied on VPN suppliers often use alternative kinds of payment - or perhaps confidential payments. Alternative forms of payments, such as accepting Bitcoin or Litecoin, aren't always confidential; usually confidential payments consist of accepting Monero cryptocurrency and cash. Depending on the user, this may not be a location of fantastic issue.
10 Best Vpn Services (2023): Security, Features + Speed
Tweaks/adjustments can be more quickly done or suggested by users ready to do so. If the VPN supplier's clients are not open-source, then it's encouraged to For example, does the VPN client app collect any gadget data? Authorizations such as bluetooth and area services gain access to should be concerned with suspicion as they are not needed to render VPN services.
Procedures Procedures are the engine behind VPN connections. Typically, centralized VPN suppliers offer numerous procedures; the user often decides which procedure to utilize. A couple of various VPN procedures exist and there is no "perfect" service; VPN companies need to offer at least User needs and requirements typically determine which protocol to select over the others (best practices when choosing a vpn provider).
Latest Posts
The Best Vpns For Small And Home-based Businesses
The Best Vpns To Protect Yourself Online
The Best Vpn App For Mobile Devices In 2023